Hola… today we would be learning some basics about data privacy of our web application database, SQL injection attacks – potential foes to web Application Database & how you can prevent yourself from SQL attacks.
Let us quickly understand what SQL is and why it is used.
Technically, SQL (Structured Query Language) is a standard language for storing, manipulating and retrieving data in databases and it allows us to interact with it. Modern web applications use databases to manage data and display dynamic content to its readers.
Let us understand what an SQL injection attack is.
SQL Injection
SQL injection or SQLi is one of the most used and most common web-based attacks. So, for an SQLi attack to work, we need a web application that uses a database. SQLi is the placement of malicious code in SQL statements, via web page input.
Consider an example where there is a web application using a database. This web application might be taking input from the user & storing the information in the database or it might be fetching data from the database and displaying out to the user. In either case, what happens is, that there is an SQL query or a database query that is generated on a Web application which is sent to the database. This query is executed on the database and relevant information is returned to the web application. Now, this is how the normal scenario is!
SQLi attack is something that can take over our database servers.
How SQL injection attack works?
Let us understand this with an example- There is a web application that takes USERNAME and PASSWORD to log in.
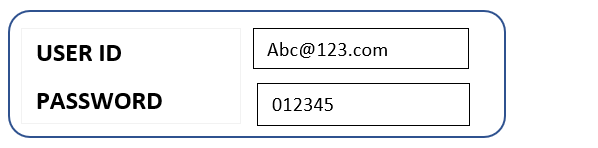
Now, the point to be kept in mind is that SQLi works only on those web application that uses a database.
The details of all the User IDs and their passwords are stored in a database in the form of a table. When you hit ENTER after typing the correct username and password, that input is sent to the database and is crosschecked with this table that is storing our credentials.
| USER ID | PASSWORD |
| Abc@123.com | 012345 |
| Xyz@456.com | 987654 |
| user@infrassist.com | pass@123 |
For a successful login, in this example, the simplest SQL query that will be generated is as follows-
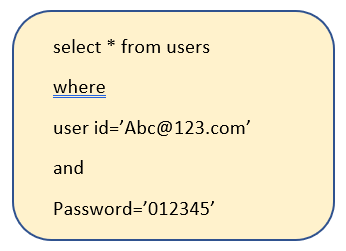
Note:
“*” – means fetch any number of rows from the database that matches some condition
“from users” – fetch the rows from the database named “users”
“where” – a condition that this user-id should have this password only.
The procedure of an SQL Injection Attack:
To perform an SQLi attack, we are interested only in the input part of the SQL query that is generated.

Here, we are now manipulating this SQL query such that it will always return TRUE (incorrect combination of credentials or complete incorrect credentials will give successful results).
For this, we will use the OR-logic gate:
| Input A | Input B | Output |
| FALSE | FALSE | FALSE |
| FALSE | TRUE | TRUE |
| TRUE | FALSE | TRUE |
| TRUE | TRUE | TRUE |
According to this logic gate, if any one of the input credentials is TRUE, irrespective of what the other credential is, the output will always be TRUE. Using this logic, the original SQL query can be now manipulated as follows:

We have set the condition here as “OR 1=1” which means- if the credentials are matched the results will be successful and even if they do not, the results will always be TRUE.
This is one such example of a malicious SQL string that can be injected to bypass the login for SQL vulnerable web applications.
More such malicious strings can be found at SQL Injection (w3schools.com)
How to Prevent SQL Injections
1. Use Prepared Statements- Alternately, you can use prepared statements to avoid SQL injections. A prepared statement is a template of an SQL query, where you specify parameters at a later stage to execute it.
- Enforcing least privilege to limit access to the database to only what is necessary.
- Performing static and dynamic testing- is a set of processes involving the verification and followed by validation of the found vulnerability.
- Using parameterized queries- A parameterized query is a type of SQL query that requires at least one parameter for execution.
- Enabling web application firewalls for extremely sensitive data.
References:
- SQL Injection (w3schools.com)
- What is SQL Injection | SQLI Attack Example & Prevention Methods | Imperva
- What is SQL Injection & How to Prevent SQL Injection (simplilearn.com)
Frequently Asked Questions
What is MySQL?
A relational database management system developed by MySQL.u003cbru003eIt stores all inputs in the form of tables and assigns key to that data.
What is Azure SQL? How does it work?
Azure is a full-featured cloud-based platform, as is common knowledge. Similar to Oracle, Azure SQL is a database server that runs entirely in the cloud and can be scaled up or down by customers based on their needs. Since it is a PaaS, most database maintenance tasks including updating, patching, backups, and monitoring are handled automatically.
What is Azure SQL Managed Instance and why use it?
An instance which combines the SQL Database with PaaS. It is one of the best options for most migrations to the cloud. It is a collection of systems and user databases. It also has a shared set of resources that is lift-and-shift ready. It helps migrate server features to the cloud with minimal hindrances.
What is the difference between Azure SQL and managed instances?
Azure SQL supports most on-premise database-level capabilities. Whereas, Managed Instance supports almost all on-premises instance-level and database-level capabilities.
How to export Azure SQL database?
There are numerous ways in which you can export Azure SQL Databases. You can export via Azure Portal to Storage Account, You can export using REST API, export via PowerShell. u003ca href=u0022https://techcommunity.microsoft.com/t5/azure-database-support-blog/export-azure-sql-database-advanced-scenarios/ba-p/3125132u0022 target=u0022_blanku0022 rel=u0022noreferrer noopeneru0022u003eThis u003c/au003eblog will give you in-depth information on each.
Upcoming
We upload a new blog on our website, every Thursday. You can explore our website to know more about us.



